Background Information
Luban Workshop is an initiative named in honour of an ancient Chinese structural engineer, inventor, and carpenter during the Zhou Dynasty. It seeks to promote cooperation between Chinese vocational training institutes and the rest of the world. China offered to cooperate with African countries by opening ten Luban workshops in the continent at the forum on China-Africa Cooperation-Beijing Summit in 2018. Machakos University was chosen to host one of the workshops making it the only institution privileged to have such a facility in Kenya and in the East African region. Machakos University in collaboration with Tianjin City Vocational College has since established the Luban Workshop training mainly in Cloud Computing and Information Security. The workshop supports training in modern technology for youth as well as promotes innovation and entrepreneurship to meet requirements of the emerging global market.
Introduction
There is a shortage of cloud computing and information security skills worldwide. Many organizations are “migrating” their operations to the cloud and are facing a challenge of finding employees or suppliers with appropriate cloud computing skills to successfully accomplish their transformation of moving to the cloud. The demand for these skills is on the rise as more and more organizations are adopting cloud services. Companies require skilled professionals in every area of Cloud Computing and information security. They need people with the skills to design and plan cloud solution architectures, manage and provision infrastructure, analyse and optimize technical and business processes, manage the implementation and ensure solution and operations reliability. It is for this reason that Machakos University established a Centre for Cloud Computing and Information Security Training. The centre provides continued education and training in building the skills of the current and future workforce to meet the demands in the field. The centre adopts a hands-on practical oriented training based on the latest technology and technology of the future

Luban Workshop also known as Cloud Computing and Information Security Training Centre is a state of the art facility and one of its own kind in Kenya and in the East African region. It has modern equipment for the most current technology. The facility is ideal for training modern skills, for research, data centre services and data recovery and backup services. It is equipped with assistance from TCVC in China through a collaborative venture (Luban Workshop). The centre is currently hosted by the department of Computing and Information Technology (CIT) in the School of Engineering and Technology.
Current and Emerging Areas in Computing
The field of Computing is very dynamic and in the last few years has experienced a number of changes – Computing has experienced a “paradigm shift”. These changes require different approaches to training and research activities. The following are the prevailing areas in research and training that are receiving a lot of attention:
- Cloud computing and Information Security
- Internet of Things(IoT)
- Big data Analytics
- Block Chain
Current Course Training programs in Machakos University
The following are the programs offered by the department of Computing and Information Technology (CIT)
- Bachelor of Science in Cloud Computing and Information Security (coming soon)
- Bachelor of Science in Computer Science
- Bachelor of Science in Information Technology
- Huawei Certified ICT Associate (HCIA) in Cloud computing (Professional Training)
- Huawei Certified ICT Associate (HCIA) in Artificial Intelligence (Professional Training)
- Huawei Certified ICT Associate(HCIA) in Datacom (Professional Training)
The centre has sub-sections that deal with Big Data Analytics, Intelligent IoT Learning sub-section, Data Centre services and Server virtualization, Data Backup and restoration, Long-range Wireless Communication Technologies including (3G, 4G and 5G Networks), Short-range wireless Communication Technologies, Block-Chain etc.

A data centre is a facility that centralizes an organization’s shared IT operations and equipment for the purposes of storing, processing, and disseminating data and applications. Since IT operations are crucial for business continuity, it generally includes redundant or backup components and infrastructure for power supply, data communication connections, environmental controls (e.g. air conditioning, fire suppression) and various security devices. Because they house an organization’s most critical and proprietary assets, data centers are vital to the continuity of daily operations.

Cloud computing is the delivery of different services through the Internet. These resources include tools and applications like data storage, servers, databases, networking, and software. Instead of keeping files on a proprietary hard drive or local storage device, cloud-based storage makes it possible to save them to a remote database. As long as an electronic device has access to the web, it has access to the data and the software programs to run it. Cloud computing is a popular option for a number of reasons including cost savings, increased productivity, speed and efficiency, performance, and security.
Cloud computing is named as such because the information being accessed is found remotely in the cloud or a virtual space. Companies that provide cloud services enable users to store files and applications on remote servers and then access all the data via the Internet. This means the user is not required to be in a specific place to gain access to it, allowing the user to work remotely from any device with which you can connect to the Internet, anywhere in the world. The Internet becomes the cloud.
Cloud computing can be both public and private. Public cloud services provide their services over the Internet for a fee. Private cloud services, on the other hand, only provide services to a certain number of people. These services are a system of networks that supply hosted services. There is also a hybrid option, which combines elements of both the public and private services.

One of the most dynamic and exciting developments in information and communications technology is the advent of the Internet of Things (IoT). Although networking technologies have become increasingly ubiquitous over the past two decades, until recently they have largely been restricted to connecting traditional end-user devices, such as mainframes, desktop and laptop computers, and, more recently, smartphones and tablets.
Recent years have witnessed the attachment of a much broader range of devices to the internet. These include vehicles, household appliances, medical devices, electric meters and controls, street lights, traffic controls, smart TVs and digital assistants. Industry analysts estimate that there are currently more than ten billion such devices connected to the internet and project that this number will increase. The increasing deployment of these devices has enabled new use cases for internet technologies. Some experts project that the IoT may generate as much as US$13 trillion in revenue by 2025.
The centre is well organised with confortable seats and tables ideal for brainstorming and discussion sessions.

The Internet of Things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet. These devices range from ordinary household objects to sophisticated industrial tools.
Over the past few years, IoT has become one of the most important technologies of the 21st century. Now that we can connect everyday objects—kitchen appliances, cars, thermostats, baby monitors—to the internet via embedded devices, seamless communication is possible between people, processes, and things.
By means of low-cost computing, the cloud, big data, analytics, and mobile technologies, physical things can share and collect data with minimal human intervention. In this hyperconnected world, digital systems can record, monitor, and adjust each interaction between connected things. The physical world meets the digital world—and they cooperate.

Big data analytics is the often complex process of examining big data to uncover information such as hidden patterns, correlations, market trends and customer preferences that can help organizations make informed business decisions.
On a broad scale, data analytics technologies and techniques provide a means to analyze data sets and take away new information—which can help organizations make informed business decisions. Business intelligence (BI) queries answer basic questions about business operations and performance.
Big data analytics is a form of advanced analytics, which involve complex applications with elements such as predictive models, statistical algorithms and what-if analysis powered by analytics systems.

Various challenges in today’s workplaces and lecture theatres such as Covid-19 prompt the need to seek digital solutions that promote effective and efficient Video Conferencing since conference rooms are where big and life-changing ideas are born. The workshop has a fully equipped meeting room with video conferencing tools that rid meetings off distractions while promoting productive discussions. The facility offers a wide range of video conferencing solutions that integrate high video with a rich audio quality to enable clear connections and collaborative sessions.
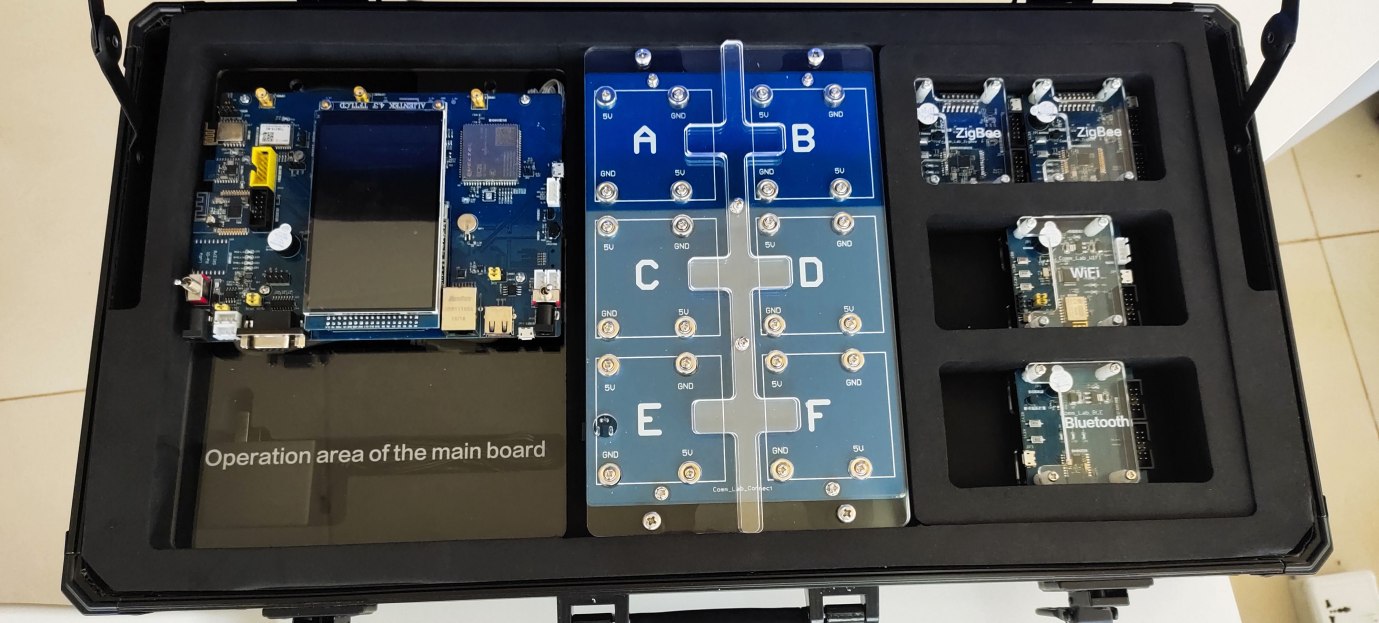
Equipment at the Centre
- FusionCompute: FusionSphere Virtualization Suite (Computer Servers in racks in the strong room)
- Short Range Wireless Communication Technology in IoT Multi-Network Full Module Communication Experiment Box
- Long Range Wireless Communication Technologies(Wi-Fi, GSM, 2G, 3G, 4G & 5G Networks)
- Donview smart board (a more efficient way to display, brainstorm and teach than traditional blackboards, with technological enhancement. Teach Technical Courses
- Handheld devices(Tablets, Smartphones)
- Computer Screens, Computer mice and keyboards
- Motion and motionless digital cameras
- Special chairs and tables ideal during experiments and brainstorming sessions
- Routers, Switches, Hubs, Cables for LAN/WLAN Construction
Technologies at the Centre
 Zigbee is an IEEE 802.15.4-based specification for a suite of high-level communication protocols used to create personal area networks with small, low-power digital radios, such as for home automation, medical device data collection, and other low-power low-bandwidth needs, designed for small scale projects
Zigbee is an IEEE 802.15.4-based specification for a suite of high-level communication protocols used to create personal area networks with small, low-power digital radios, such as for home automation, medical device data collection, and other low-power low-bandwidth needs, designed for small scale projects
 Bluetooth is a wireless technology standard used for exchanging data between fixed and mobile devices over short distances using UHF radio waves in the industrial, scientific and medical radio bands, from 2.402 GHz to 2.480 GHz, and building personal area networks (PANs).
Bluetooth is a wireless technology standard used for exchanging data between fixed and mobile devices over short distances using UHF radio waves in the industrial, scientific and medical radio bands, from 2.402 GHz to 2.480 GHz, and building personal area networks (PANs).
 Z-Wave is a wireless communications protocol used primarily for home automation. It is a mesh network using low-energy radio waves to communicate from appliance to appliance, allowing for wireless control of residential appliances and other devices, such as lighting control, security systems, thermostats, windows, locks, swimming pools and garage door openers. A Z-Wave system can be controlled via the Internet from a smart phone, tablet or computer, and locally through a smart speaker.
Z-Wave is a wireless communications protocol used primarily for home automation. It is a mesh network using low-energy radio waves to communicate from appliance to appliance, allowing for wireless control of residential appliances and other devices, such as lighting control, security systems, thermostats, windows, locks, swimming pools and garage door openers. A Z-Wave system can be controlled via the Internet from a smart phone, tablet or computer, and locally through a smart speaker.
 FusionSphere Virtualization Suite virtualizes hardware resources using the virtualization software deployed on physical servers, so that one physical server can function as multiple virtual servers.
FusionSphere Virtualization Suite virtualizes hardware resources using the virtualization software deployed on physical servers, so that one physical server can function as multiple virtual servers.
9
FusionSphere maximizes resource utilization by consolidating existing workloads on a smaller number of servers and is therefore able to release more servers to carry new workloads.
 Wi-Fi is a wireless networking technology that allows devices such as computers (laptops and desktops), mobile devices (smart phones and wearables), and other equipment (printers and video cameras) to interface with the Internet. It allows these devices–and many more–to exchange information with one another, creating a network.
Wi-Fi is a wireless networking technology that allows devices such as computers (laptops and desktops), mobile devices (smart phones and wearables), and other equipment (printers and video cameras) to interface with the Internet. It allows these devices–and many more–to exchange information with one another, creating a network.
 The Global System for Mobile Communications (GSM) is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation (2G) digital cellular networks used by mobile devices such as mobile phones and tablets.
The Global System for Mobile Communications (GSM) is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation (2G) digital cellular networks used by mobile devices such as mobile phones and tablets.
 A blockchain is a digital record of transactions. The name comes from its structure, in which individual records, called blocks, are linked together in single list, called a chain. Blockchains are used for recording transactions made with cryptocurrencies, such as Bitcoin, and have many other applications. Each transaction added to a blockchain is validated by multiple computers on the Internet.
A blockchain is a digital record of transactions. The name comes from its structure, in which individual records, called blocks, are linked together in single list, called a chain. Blockchains are used for recording transactions made with cryptocurrencies, such as Bitcoin, and have many other applications. Each transaction added to a blockchain is validated by multiple computers on the Internet.
 General Packet Radio Services (GPRS) is a packet-based wireless communication service that promises data rates from 56 up to 114 Kbps and continuous connection to the Internet for mobile phone and computer users. The higher data rates allow users to take part in video conferences and interact with multimedia Web sites and similar applications using mobile handheld devices as well as notebook computers.
General Packet Radio Services (GPRS) is a packet-based wireless communication service that promises data rates from 56 up to 114 Kbps and continuous connection to the Internet for mobile phone and computer users. The higher data rates allow users to take part in video conferences and interact with multimedia Web sites and similar applications using mobile handheld devices as well as notebook computers.

A blockchain is a permanent, sequential list of transaction records distributed over a network. Each block in the chain contains a hash of the previous block, along with a timestamp and transaction data. This makes the blockchain inherently resistant to attack or manipulation.
Blockchain technology is ideal for recording various types of transactions where data is sensitive or targeted by hackers for unauthorized duplication or other fraudulent activity. Bitcoin and other cryptocurrencies use blockchain technology to record transactions. Blockchain for business applications can include recording of contracts, medical records, monetary transactions and much more.
Cryptography is the study and practice of securing private messages so that they can only be read by the intended parties. It involves encrypting and decrypting content using various methods and encryption keys. An unintended third party would not be able to understand the message without the proper key to decode it. Modern cryptography has grown to include many sub-fields of study such as data integrity and user authentication and is vital to ecommerce, banking and much more.
Blockchain technology is growing in use and it’s essential to understand its core business uses and benefits. The courses are designed to help both technical and nontechnical audiences learn the key concepts behind hyperledger and blockchain, making clear the various enterprise applications. Students learn about current hyperledger projects and business use cases and even get hands-on experience implementing basic blockchains.

Entrepreneurship refers to an individual’s ability to turn ideas into action. Entrepreneurial programmes and modules offer students the tools to think creatively and to be an effective problem solver. Education for entrepreneurship can be particularly effective in initialvocational training, as students are close to entering working life and self-employment may be a valuable option for them. Students are taught ways in which innovations in higher and vocational education develop competencies for entrepreneurship, enterprising behaviour and employability.
Regardless of the vocational training area, the most effective way to teach entrepreneurship is to have students participate in practical projects and activities, in which learning by doing is emphasised and real experience with entrepreneurship is gained. Problem-driven and experience-oriented education is essential to fostering entrepreneurial mindsets and abilities in the workshop.
